There are two primary areas to configure when deciding who should see or have CRUD (create, read, update, delete) access to one of your applications. These two areas are the application and the table, explained below:
1. The Application
The application is what users see on the left hand navigator. The primary application (container) is called the application record, where all the links within it are referred to as modules. Access to an entire application, or different individual modules is defined by the role on either the application or module record.
If you want to add users to being able to see an application, you would either:
a. Add different roles to the application that the users have (e.g. itil).
b. Remove all roles that are currently listed. This will grant visibility to all users, including end users.
The fastest way to configure the application is to type sys_app_application.list into your navigator and press enter.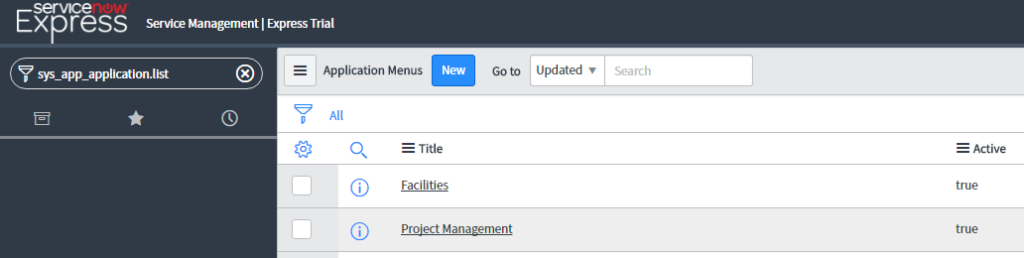
Then, edit the Roles required for either that application, or one of the modules in the application’s related list. 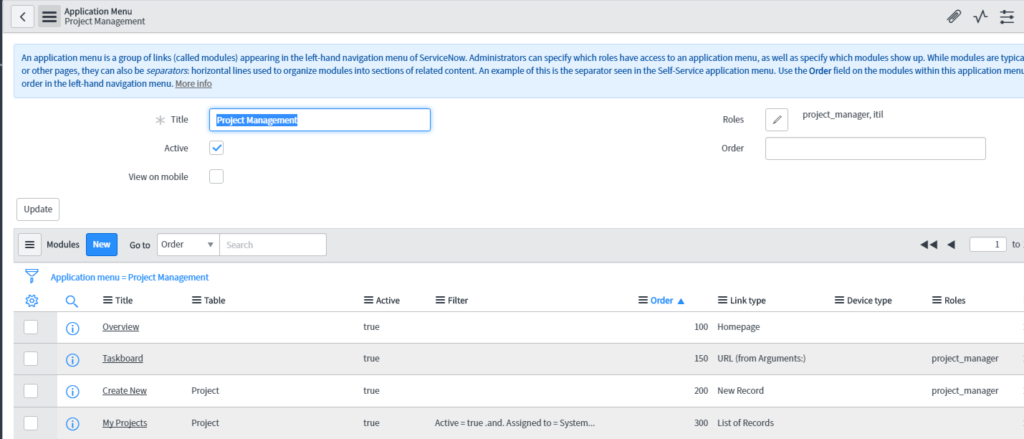
2. The Actual Table
When you limit a users access to an application, you are simply removing it from the navigator. The underlying actions on the table are not yet secured. For example, if you simply add an itil role to the application, an end user may still have access by typing the tablename.list into the navigator, if you did not restrict table access. So how do you limit table access?
Simply navigate to the Manage Table module in your instance, and select the table of your choice. 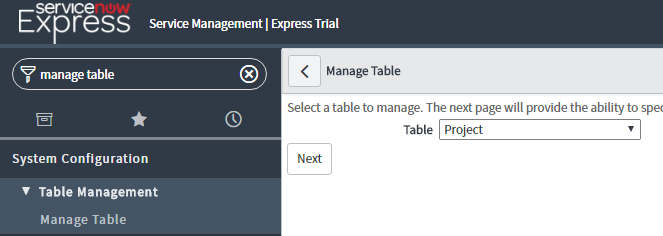
There, you will see roles required for create, write, read, and delete access. If a user has any of the roles listed for the given level of access, they will be granted access to that operation. In addition, if no roles are entered, all users will have access to the given operation. 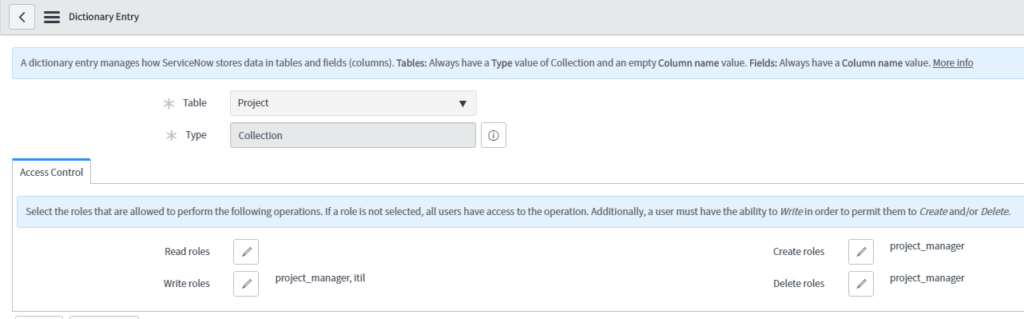
As a reminder, if you open access to ‘end users’ to work in the application, they will be considered ‘fulfillers’.